In Cybersecurity
How the nationally-recognized NIST Framework can bolster your Cybersecurity?

CEO
If you are like most of the business leaders we talk to, you already know that cyber security is critically important. You've probably sat in on a handful cyber security presentations and seminars, you know some details about GPDG, CCPA, and maybe even CMMC, but despite all the time you have already invested you still probably don't have clarity on how secure your organization is today and what cyber security controls are most important for your protection.
This article is to answer those central questions and introduce you to the security framework globally accepted by cyber security experts.

National Institute of Standards and Technology (NIST)
Just like accountants reference GAAP and manufacturing companies look to ISO for making critical business decisions, cybersecurity professionals look to the National Institute of Standards and Technology, or NIST, to rate the effectiveness of an organization's cybersecurity program.
NIST CSF
The NIST cybersecurity framework, or NIST CSF, is the de-facto standard for countering cybersecurity threats, and its prescriptive framework offers highly-specific guidance on the exact steps you need to take to secure your organization.
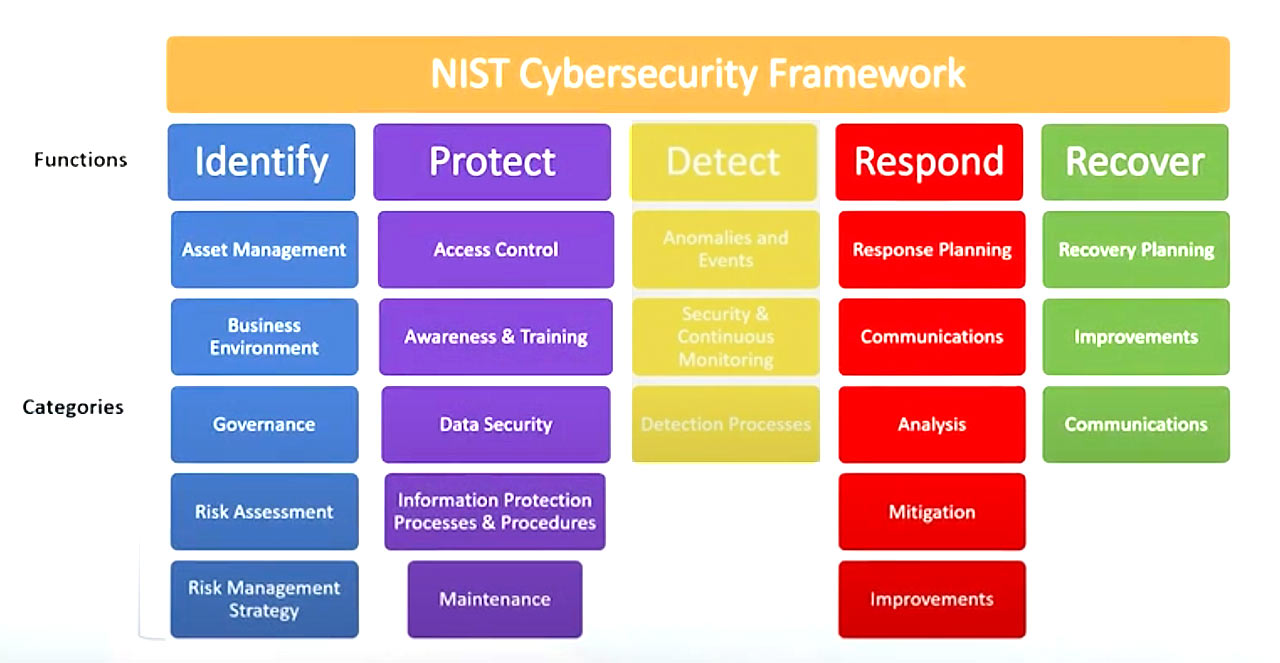
The NIST CSF applies to every industry, as it is the foundation upon which industry-specific guidelines like HIPAA, PCI and CMMC get their recommendations, but it is particularly helpful for non-regulated industries that are looking for a proven and authoritative framework to align with.
Center for Internet Security CIS TOP-20
The original NIST publication contained over a thousand controls and, although helpful, it was not digestible for typical small business. The Center for Internet Security, an organization that promotes the application of cybersecurity best practices, orchestrated a large crowdsourced effort to streamline the NIST publication into a prioritized list of cybersecurity controls, now commonly referred to as the CIS TOP-20 controls, which are the most effective defensive actions an organization can implement to improve their security posture.

These TOP-20 controls are now globally accepted as the crucial starting point for any cyber defense strategy. So, what does this all mean and what are cyber savvy organizations doing as a result?
Step 1
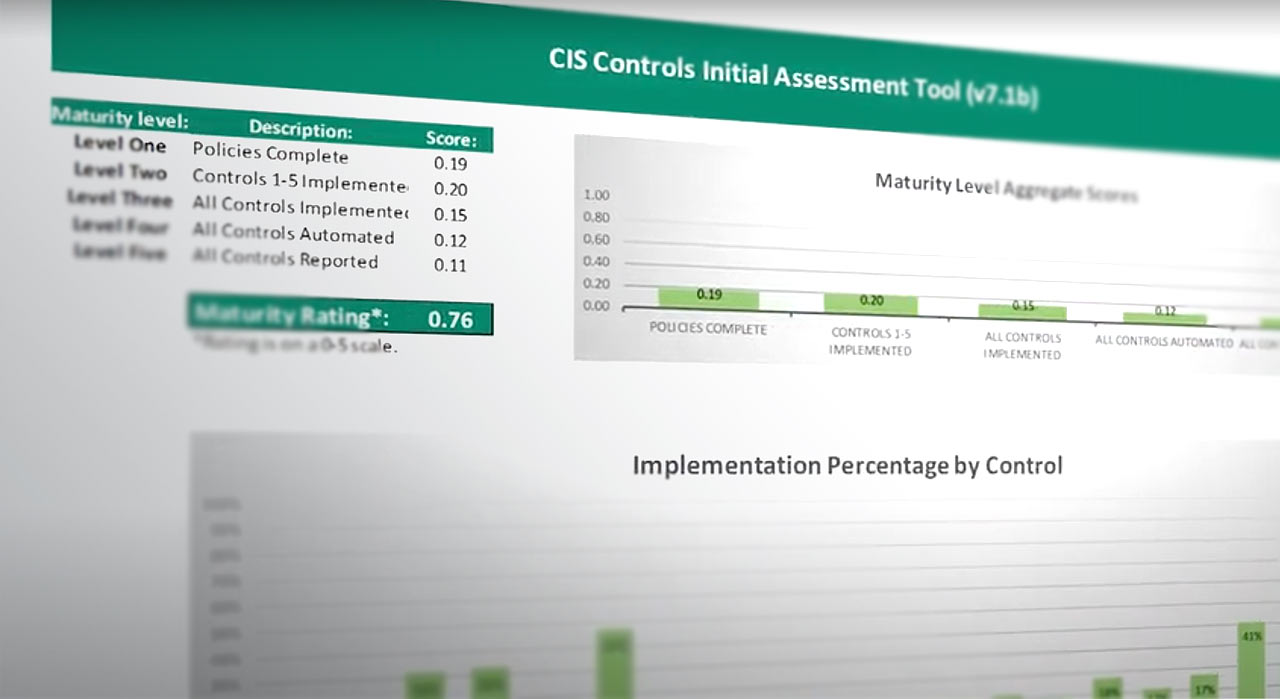
At the risk of sounding a bit self-serving, the first step is to find a cyber security expert like TechMD and conduct what is known as a "security maturity level assessment". This audit involves interviews with key company personnel and review of the CIS TOP-20 controls to see which controls have and have not yet been implemented by your organization.
Upon conclusion of the assessment you will then have a clear picture of your organization's most critical cyber security vulnerabilities and a security maturity level score of zero to five, that you can compare across your industry.
Step 2
Step two is to decide what security maturity level is appropriate for your organization and create a prioritized action plan that will get you there. This plan is then implemented over time through a combination of IT projects, changes and IT policies under the direction of a Cybersecurity expert.
Your improved security maturity level score is ultimately certified by a third party accounting firm and can be used to demonstrate your organization's cybersecurity posture with customers, vendors and insurance providers.
The process is straightforward, but can be complex to integrate into your specific organization's IT infrastructure and systems. The good news, however, is that you can make progress at your own pace and budget, and even a little progress can have a huge impact.
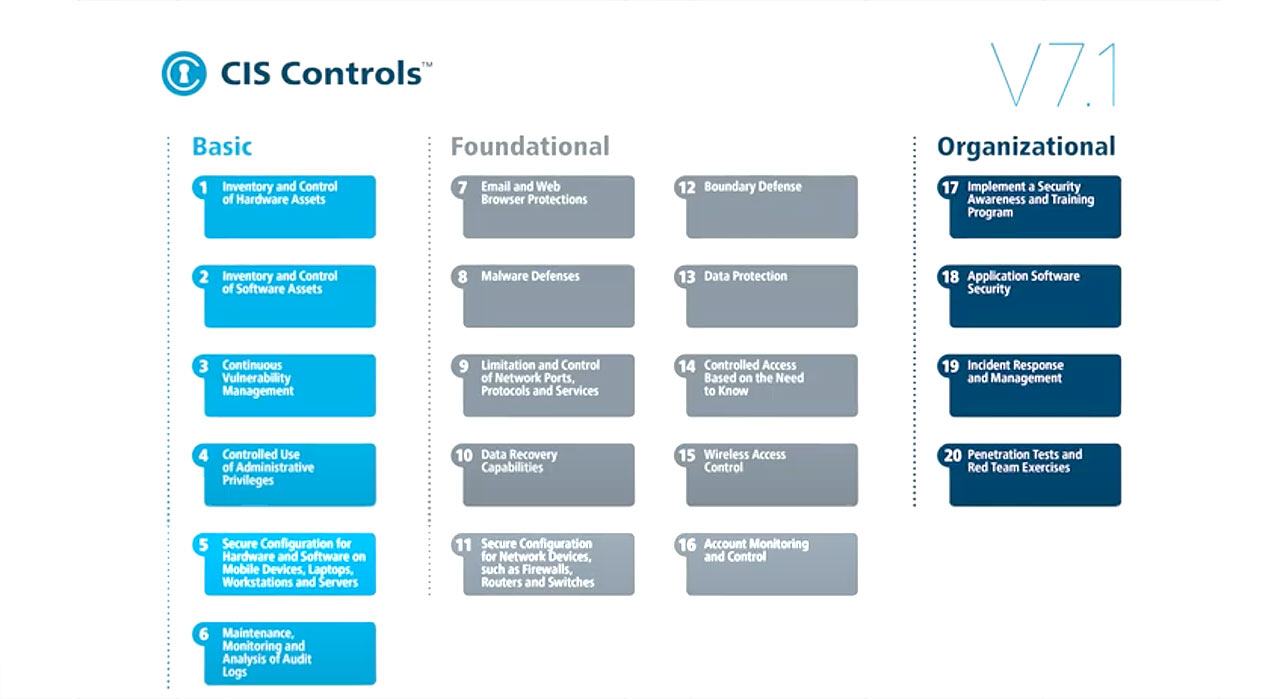
For example, a study found that implementing just the top 5 CIS controls prevents 85% of attacks, while the top 20 CIS controls prevent 97% of attacks. Obviously, this framework is not exclusive to TechMD, but if you would like to learn more about what a security maturity level assessment looks like for your business please send us an email.
We have already been implementing security maturity level assessments for our clients for a while now, and have a standartized process and dedicated Cybersecurity team that can walk you through the process.

